HMT Release 10.5 Notes
Release Notes HMT-1 version 10.5.0
1. Release Overview
This Release Notes document is for the RealWear HMT-1 firmware release 10.5.0, a security patch release with additional updates.
The release is only applicable to the HMT-1 standard model. Any HMT-1 ever sold by RealWear may update to this release (although earlier updates may need to be installed before 10.5.0 can be installed.)
1.1 Deliverables
| Delivery Data | |
| Company | RealWear Inc. |
| Model Number | HMT-1 (T1100G) |
| Firmware Version | 10.5.0 |
| Build File Name | 10.5.0-04-C.HMT-1.G |
2. Release Notes
2.1 Translation Changes
2.1.1 Translation Updates
Improvements have been made to Chinese, French, German, Italian, Japanese, Korean, Polish, Portuguese, and Thai. This includes some global commands, so please review the 10.5.0 User Guides for more detailed information, available at https://realwear.com/support/.
2.2 Security Changes
2.2.1 Android Security Updates
Security updates released through the end of June 2019 are incorporated into this release. See the full list of updates in Appendix 1 of this document.
2.3 Developer Changes
2.3.1 Software Key Update
The key used for software signing has been updated with this release. If you use the RealWear Explorer application you will need to upgrade to the newest version, 4.1.0. Please visit https://realwear.com/knowledge-center/developer/rw-explorer/ to download and see additional information.
2.4 Bug Fix Highlights
2.4.1 Document Viewer
The ‘Go to page #’ voice command now works properly in Japanese. Also addressed a general crash when opening files.
2.4.2 General
Global commands now disabled while device is locked in the Secure Boot mode and voice command to disable an application’s notifications now works properly.
2.4.3 ISV Application Interaction
Addressed some stability issues when working with SureLock or text edit fields. Addressed a field focus issue when interacting with the Video Assist app.
Updated HTML JS plugin and other developer resources. See https://realwear.com/knowledge-center/developer/ for more information.
2.4.4 Bug Summary
Issues addressed by component/app; details available on request:
3 Camera issues
2 WearHF issue
7 My Files issues
3 Developer Tools issues
2 Document Viewer issues
2 My Controls issues
4 Keyboard issues
4 General issues
3. Software Update Method
Please follow the instructions provided for updating in the Wireless Update article.
Android Security Bulletin — April 2019
* = not publicly available
Framework
| CVE | References | RealWear Update |
| CVE-2019-2026 | A-120866126* | N/A to RealWear kernel version |
Media Framework
| CVE | References | RealWear Update |
| CVE-2019-2027 | A-119120561 | Included |
| CVE-2019-2028 | A-120644655 | Included |
System
| CVE | References | RealWear Update |
| CVE-2019-2030 | A-119496789 | N/A to RealWear kernel version |
| CVE-2019-2031 | A-120502559 | Included |
| CVE-2019-2033 | A-121327565 [2] | N/A to RealWear kernel version |
| CVE-2019-2034 | A-122035770 | Included |
| CVE-2019-2035 | A-122320256 | Included |
| CVE-2019-2038 | A-121259048 | Included |
| CVE-2019-2039 | A-121260197 | Included |
| CVE-2019-2040 | A-122316913 | N/A to RealWear kernel version |
| CVE-2019-2029 | A-120612744 | Included |
| CVE-2019-2032 | A-121145627 | Included |
| CVE-2019-2041 | A-122034690 [2] [3] | N/A to RealWear kernel version |
| CVE-2019-2037 | A-119870451 | Included |
Qualcomm components
| CVE | References | RealWear Update |
| CVE-2018-11940 | A-79377832 QC-CR#2254946 | N/A to RealWear kernel version |
| CVE-2017-17772 | A-72957385 QC-CR#2153003 [2] | N/A to RealWear kernel version |
| CVE-2018-11294 | A-109741680 QC-CR#2197481 | Included |
| CVE-2018-5855 | A-77527719 QC-CR#2193421 | N/A to RealWear kernel version |
| CVE-2018-11299 | A-109741946 QC-CR#2186953 | N/A to RealWear kernel version |
| CVE-2018-11826 | A-111127853 QC-CR#2205957 | N/A to RealWear kernel version |
| CVE-2018-11827 | A-111128575 QC-CR#2206569 | N/A to RealWear kernel version |
| CVE-2018-11840 | A-111126050 QC-CR#2215443 | N/A to RealWear kernel version |
| CVE-2018-11851 | A-111125792 QC-CR#2221902 | N/A to RealWear kernel version |
| CVE-2018-11860 | A-111128301 QC-CR#2225113 | Included |
| CVE-2018-11868 | A-111128420 QC-CR#2227248 | N/A to RealWear kernel version |
| CVE-2018-11869 | A-111128838 QC-CR#2227263 | N/A to RealWear kernel version |
| CVE-2018-11878 | A-111128797 QC-CR#2228608 | Included |
| CVE-2018-11889 | A-111128421 QC-CR#2230998 | N/A to RealWear kernel version |
| CVE-2018-11891 | A-111128578 QC-CR#2231767 | N/A to RealWear kernel version |
| CVE-2018-11894 | A-111127989 QC-CR#2232358 | N/A to RealWear kernel version |
| CVE-2018-11895 | A-111128877 QC-CR#2232542 | N/A to RealWear kernel version |
| CVE-2018-11897 | A-111128841 QC-CR#2233033 | N/A to RealWear kernel version |
| CVE-2018-11902 | A-111126532 QC-CR#2225604 | N/A to RealWear kernel version |
| CVE-2018-11904 | A-111125111 QC-CR#2215446 | Included |
| CVE-2018-11905 | A-112277221 QC-CR#2146878 | N/A to RealWear kernel version |
| CVE-2018-11923 | A-112276863 QC-CR#2224443 | N/A to RealWear kernel version |
| CVE-2018-11924 | A-112278150 QC-CR#2224451 | N/A to RealWear kernel version |
| CVE-2018-11925 | A-112277910 QC-CR#2226375 [2] | N/A to RealWear kernel version |
| CVE-2018-11927 | A-112277186 QC-CR#2227076 | Included |
| CVE-2018-11930 | A-112278861 QC-CR#2231770 | N/A to RealWear kernel version |
| CVE-2018-11937 | A-112277891 QC-CR#2245944 | N/A to RealWear kernel version |
| CVE-2018-11949 | A-112278405 QC-CR#2249815 | N/A to RealWear kernel version |
| CVE-2018-11953 | A-112277852 QC-CR#2235576 | Included |
| CVE-2018-13920 | A-120487136* QC-CR#2293841 | N/A to RealWear kernel version |
Qualcomm closed-source components
| CVE | References | RealWear Update |
| CVE-2018-11271 | A-120487384* 2000243 | Included |
| CVE-2018-11976 | A-117119000* 2236670 | N/A to RealWear kernel version |
| CVE-2018-12004 | A-117118976* 2238830 | N/A to RealWear kernel version |
| CVE-2018-13886 | A-117118295* 2283594 | Included |
| CVE-2018-13887 | A-117119172* 2283883 | Included |
| CVE-2019-2250 | A-122473270* | N/A to RealWear kernel version |
| CVE-2018-11291 | A-109678120* 2040181 | N/A to RealWear kernel version |
| CVE-2018-11821 | A-111093019* 2187755 | N/A to RealWear kernel version |
| CVE-2018-11822 | A-111092813* 2187762 | N/A to RealWear kernel version |
| CVE-2018-11828 | A-111089816* 2207092 | Included |
| CVE-2018-11849 | A-111092945* 2221140 | N/A to RealWear kernel version |
| CVE-2018-11850 | A-111092919* 2221167 | N/A to RealWear kernel version |
| CVE-2018-11853 | A-111091938* 2222017 | N/A to RealWear kernel version |
| CVE-2018-11854 | A-111093762* 2222191 | N/A to RealWear kernel version |
| CVE-2018-11856 | A-111093242* 2222834 | N/A to RealWear kernel version |
| CVE-2018-11859 | A-111090373* 2224519 | N/A to RealWear kernel version |
| CVE-2018-11861 | A-111092814* 2226054 | N/A to RealWear kernel version |
| CVE-2018-11862 | A-111093763* 2226058 | N/A to RealWear kernel version |
| CVE-2018-11867 | A-111093243* 2227112 | N/A to RealWear kernel version |
| CVE-2018-11870 | A-111089817* 2227395 | N/A to RealWear kernel version |
| CVE-2018-11871 | A-111092400* 2227815 | N/A to RealWear kernel version |
| CVE-2018-11872 | A-111090534* 2227853 | N/A to RealWear kernel version |
| CVE-2018-11873 | A-111091378* 2228223 | N/A to RealWear kernel version |
| CVE-2018-11874 | A-111092946* 2228284 | N/A to RealWear kernel version |
| CVE-2018-11875 | A-111093022* 2228325 | N/A to RealWear kernel version |
| CVE-2018-11876 | A-111093244* 2228496 | N/A to RealWear kernel version |
| CVE-2018-11877 | A-111092888* 2228548 | N/A to RealWear kernel version |
| CVE-2018-11879 | A-111093280* 2228625 | N/A to RealWear kernel version |
| CVE-2018-11880 | A-111092401* 2228951 | N/A to RealWear kernel version |
| CVE-2018-11882 | A-111093259* 2229290 | N/A to RealWear kernel version |
| CVE-2018-11884 | A-111090535* 2229693 | N/A to RealWear kernel version |
| CVE-2018-11928 | A-112279580* 2229682 | N/A to RealWear kernel version |
| CVE-2018-11936 | A-112279127* 2245122 | N/A to RealWear kernel version |
| CVE-2018-11967 | A-119049704* 2252256 | Included |
| CVE-2018-11967 | A-119052960* | N/A to RealWear kernel version |
| CVE-2018-11968 | A-114042276* 2187717 | N/A to RealWear kernel version |
| CVE-2018-12005 | A-117118499* 2246561 | Included |
| CVE-2018-12012 | A-117119174* 2276825 | N/A to RealWear kernel version |
| CVE-2018-12013 | A-117119152* 2277575 | N/A to RealWear kernel version |
| CVE-2018-13885 | A-117118789* 2282695 | Included |
| CVE-2018-13895 | A-122472377* | N/A to RealWear kernel version |
| CVE-2018-13925 | A-120483842* 2318550 | Included |
| CVE-2019-2244 | A-122472139* | N/A to RealWear kernel version |
| CVE-2019-2245 | A-122473145* | N/A to RealWear kernel version |
Android Security Bulletin — May 2019
System
| CVE | References | RealWear Update |
| CVE-2019-2043 | A-120484087 | Included |
| CVE-2019-2044 | A-123701862 | Included |
| CVE-2019-2045 | A-117554758 | Included |
| CVE-2019-2046 | A-117556220 | Included |
| CVE-2019-2047 | A-117607414 | Included |
| CVE-2019-2049 | A-120445479 | N/A to RealWear kernel version |
| CVE-2019-2050 | A-121327323 | Included |
| CVE-2019-2051 | A-117555811 | Included |
| CVE-2019-2052 | A-117556606 | Included |
| CVE-2019-2053 | A-122074159 | Included |
Qualcomm components
| CVE | References | RealWear Update | |
| CVE-2018-11955 | A-78528839 QC-CR#2249768 | N/A to RealWear kernel version | |
| CVE-2018-13919 | A-120486022 QC-CR#2289598 | Included | |
Qualcomm closed-source components
| CVE | References | RealWear Update |
| CVE-2018-5912 | A-114074547* | N/A to RealWear kernel version |
| CVE-2018-13898 | A-119050181* 2299768 | N/A to RealWear kernel version |
| CVE-2019-2255 | A-122474428* 2343530 | Included |
| CVE-2019-2256 | A-114067283* 2346901 | Included |
| CVE-2018-13901 | A-119049466* 2309910 | Included |
| CVE-2018-13902 | A-119050073* 2287717 | Included |
| CVE-2018-13906 | A-119049388* 2218432 | N/A to RealWear kernel version |
| CVE-2018-13907 | A-119050001* 2289607 | N/A to RealWear kernel version |
| CVE-2018-13908 | A-119049623* 2300079 | N/A to RealWear kernel version |
| CVE-2018-13909 | A-119051002* 2255321 | N/A to RealWear kernel version |
| CVE-2018-13910 | A-119050182* 2288656 | N/A to RealWear kernel version |
| CVE-2018-13911 | A-119052037* 2287702 | Included |
| CVE-2018-5913 | A-122472140* 2254550 2218372 | Included |
| CVE-2019-2257 | A-112303441* 2236511 | Included |
| CVE-2019-2259 | A-123997497* 2344295 | N/A to RealWear kernel version |
Android Security Bulletin — June 2019
Framework
| CVE | References | RealWear Update |
| CVE-2019-2090 | A-128599183 | Included |
| CVE-2019-2091 | A-128599660 | Included |
| CVE-2019-2092 | A-128599668 | Included |
| CVE-2018-9526 | A-112159033 [2] [3] [4] | Included |
Media Framework
| CVE | References | RealWear Update |
| CVE-2019-2093 | A-119292397 | N/A to RealWear kernel version |
| CVE-2019-2094 | A-129068792 | Included |
| CVE-2019-2095 | A-124232283 | N/A to RealWear kernel version |
| CVE-2019-2096 | A-123237974 [2] | Included |
System
| CVE | References | RealWear Update |
| CVE-2019-2097 | A-117606285 | Included |
| CVE-2019-2102 | A-128843052 | Included |
| CVE-2019-2098 | A-128599467 | Included |
| CVE-2019-2099 | A-123583388 | Included |
Kernel
| CVE | References | RealWear Update |
| CVE-2019-2101 | A-111760968* | Included |
Qualcomm components
| CVE | References | RealWear Update |
| CVE-2019-2269 | A-123700924 QC-CR#2264429 | N/A to RealWear kernel version |
| CVE-2019-2287 | A-114399807 QC-CR#2368791 [2] | Included |
| CVE-2019-2260 | A-123999895 QC-CR#2294824 | N/A to RealWear kernel version |
| CVE-2019-2292 | A-127513046 QC-CR#2327688 QC-CR#2333042 | N/A to RealWear kernel version |
Qualcomm closed-source components
| CVE | References | RealWear Update |
| CVE-2018-13924 | A-120486477* 2331078 | N/A to RealWear kernel version |
| CVE-2018-13927 | A-120485121* 2330128 | N/A to RealWear kernel version |
| CVE-2018-13896 | A-120487163* 2263692 | N/A to RealWear kernel version |
| CVE-2019-2243 | A-122473494* | N/A to RealWear kernel version |
| CVE-2019-2261 | A-123998003* 2235853 | Included |
Release Notes HMT-1Z1 version 10.4.0
1. Release Overview
This Release Notes document is for the RealWear HMT-1Z1 firmware release 10.4.0, a quarterly security patch release with additional feature updates.
The release is only applicable to the HMT-1 standard model. Any HMT-1Z1 ever sold by RealWear may update to this release (although earlier updates may need to be installed before 10.4.0 can be installed). To update to version 10.4.0 the HMT must be on version 10.1.0-10-C.HMT-1Z1.S.
1.1 Deliverables
| Delivery Data | |
| Company | RealWear Inc. |
| Model Number | HMT-1Z1 (T1100S) |
| Firmware Version | 10.4.0 |
| Build File Name | 10.4.0-01-C.HMT-1Z1.S |
2 Release Notes
2.1 New Features
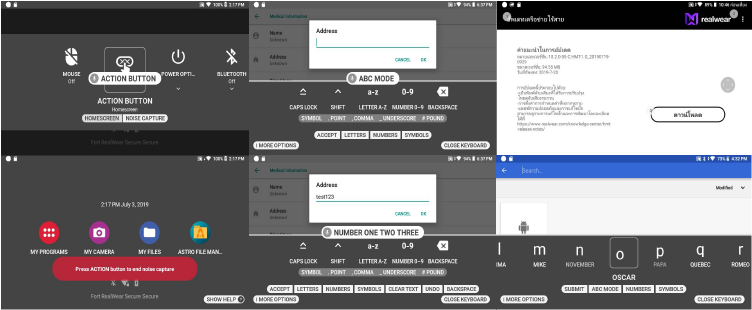
2.1.1 Updated Voice Keyboard Enables ABC Mode
The HMT end user may now call out independent letters in “ABC” mode. In the keyboard, say “ABC” to activate this mode then say “Letter C A T” to spell “cat”. Users may continue to use the present mode of saying the NATO code-word for each letter.
2.1.2 End-User Action Button Control Mapping / Noise Capture Mode
As of Release 10.4.0, RealWear is permitting limited use of action button functionality by users (previously developers had some control over action button functionality). Available on the My Controls list is an “Action Button” mapping selection. The current default behavior – return to the Home Screen – will still be available, but a new mapping is available called Noise Capture.
Setting the Action Button to Noise Capture mode enables the HMT end user to toggle noise cancellation by depressing Action Button. When an end user enables Noise Capture, all ambient noise captured by HMT microphones is fed into the primary sound input channel for any application so that audio is captured; for example, machinery sounds, a nearby person’s speech, or environmental sounds are accurately represented and/or recorded.
2.2 General Changes
2.2.1 Remove Snap from List Controls
As part of the continual tuning of the user experience, this version includes changes in how list controls such as My Controls and My Camera’s More Options behave. The scrolling motion is now continuous and smooth instead of snapping into a partial lock on the in-focus selection.
2.3 Translation Changes
2.3.1 Various Translation Updates
Improvements have been made in Polish, Korean, Spanish, Chinese, Thai, German, and Japanese. Details are listed in an appendix below.
2.4 Security Changes
2.4.1 Android Security Updates
Security updates released through the end of March 2019 are incorporated into this release. See the full list of updates in the appendix below.
2.4.2 Encryption and PIN Unlock Screen
When an HMT has had full-device encryption activated and is PIN protected, a special PIN unlock screen appears when powered on. This screen contains all ten possible numerals with code words randomly assigned to each numeral.
The secure scroll keyboard continues to be used for simple screen unlocking.
2.5 Configuration Changes
2.5.1 Modification of the Home Screen and Lock Screen Backgrounds
Previously, the home screen and lock screen backgrounds were locked on all HMTs. With this release, an organization may change either background on any fully branded RealWear device. Note: Co-branded devices may not have this capability unlocked.
2.5.2 Home Screen App Configuration
The default view of the Home Screen (My Programs, My Camera, and My Files) may be modified. Up to five apps may be placed in any order on the home screen.
2.5.3 Storage Locations for Camera Photos and Videos
The location for storing photos and videos recorded by the HMT camera may be modified via configuration settings.
2.5.4 Configure the Visible Folders at the Top Level of My Files
The HMT may be configured to show any specified folder in the user data partition. The traditional folders, “My Media”, “My Photos”, and “My Documents” may be retained or replaced in the folder list. A custom folder icon may be included with the configuration.
2.5.5 Whitelist / Blacklist Items in My Programs
A hardware support professional may determine what apps appear in the My Programs page either by creating a whitelist or blacklist. All programs that are shown on the My Programs screen by default will continue to appear except for the items placed in the blacklist.
2.5.6 Whitelist / Blacklist Items in My Controls
A hardware support professional may determine what control items appear in the My Controls list either by creating a whitelist or a blacklist. The list will retain all default controls except for the items placed in the blacklist.
2.5.7 Control Item for Launching My Programs
A control to navigate to the My Programs page may be added to the My Controls whitelist in the case when the My Programs icon has been removed from the Home Screen. This control is not available by default.
2.5.8 Language String Override
Any string in the HMT-1Z1 operating system or RealWear core applications may be modified, thereby allowing customization of existing commands with any desired label. In many cases, organizations may prefer different translations of commands. This ability can be used on any currently supported language, including English. For a list of supported languages, please refer to the RealWear Knowledge Center at www.realwear.com/knowledge-center/.
2.5.9 Language Selector List Configuration
The HMT-1Z1 ships with 12 languages that may be selected in real time. However, to make language changes easier and faster, HMTs may be configured to show only a subset of the languages and may be set in any desired order.
2.5.10 Maximum Volume Level Setting
The maximum volume of both the speaker and audio port may be reduced via configuration settings.
2.6 Developer Changes
2.6.1 Added Support for File Providers in Camera Applet
It is now possible to pass a file provider to the camera applet to specify the file to use when capturing images and videos. The previous method of passing a URI to a file is not supported past Android SDK 24.
To support developers, an update has been made to the developer sample app to show how to capture video.
2.7 Bug Fixes
A full list of resolved bugs is in Appendix 3 of this document.
3 Software Update Method
Please follow the instructions provided for updating in the Wireless Update article.
Android Security Bulletin — January 2019
Framework
| CVE | References | RealWear Update |
| CVE-2018-9582 | A-112031362 | Included |
System
| CVE | References | RealWear Update | |
| CVE-2018-9583 | A-112860487 | Included | |
| CVE-2018-9584 | A-114047681 | Included | |
| CVE-2018-9585 | A-117554809 | Included | |
| CVE-2018-9586 | A-116754444 | Included | |
| CVE-2018-9587 | A-113597344 | Included | |
| CVE-2018-9588 | A-111450156 | Included | |
| CVE-2018-9589 | A-111893132 | Included | |
| CVE-2018-9590 | A-115900043 | Included | |
| CVE-2018-9591 | A-116108738 | Included | |
| CVE-2018-9592 | A-116319076 | Included | |
| CVE-2018-9593 | A-116722267 | Included | |
| CVE-2018-9594 | A-116791157 | Included | |
Kernel components
| CVE | References | RealWear Update |
| CVE-2018-10876 | A-116406122 Upstream kernel | Included |
| CVE-2018-10880 | A-116406509 Upstream kernel | N/A to RealWear kernel version |
| CVE-2018-10882 | A-116406626 Upstream kernel | Included |
| CVE-2018-13405 | A-113452403 Upstream kernel | Included |
| CVE-2018-18281 | A-118836219 Upstream kernel | N/A to RealWear kernel version |
| CVE-2018-17182 | A-117280327 Upstream kernel | Included |
| CVE-2018-10877 | A-116406625 Upstream kernel | Included |
Qualcomm components
| CVE | References | RealWear Update |
| CVE-2018-11962 | A-117118292 QC-CR#2267916 | Included |
| CVE-2018-12014 | A-117118062 QC-CR#2278688 | Included |
| CVE-2018-13889 | A-117118677 QC-CR#2288358 | Included |
Qualcomm closed-source components
| CVE | References | RealWear Update |
| CVE-2018-11847 | A-111092812* | Included |
| CVE-2018-11888 | A-111093241* | N/A to RealWear kernel version |
| CVE-2018-13888 | A-117119136* | N/A to RealWear kernel version |
Android Security Bulletin — February 2019
Framework
| CVE | References | RealWear Update |
| CVE-2019-1986 | A-117838472 [2] | N/A to Android 8.1 |
| CVE-2019-1987 | A-118143775 [2] | Included |
| CVE-2019-1988 | A-118372692 | Included |
Library
| CVE | References | RealWear Update |
| CVE-2017-17760 | A-78029030* | N/A to RealWear Android baseline |
| CVE-2018-5268 | A-78029634* | N/A to RealWear Android baseline |
| CVE-2018-5269 | A-78029727* | N/A to RealWear Android baseline |
| CVE-2017-18009 | A-78026242* | N/A to RealWear Android baseline |
System
| CVE | References | RealWear Update |
| CVE-2019-1991 | A-110166268 | Included |
| CVE-2019-1992 | A-116222069 | Included |
| CVE-2019-1993 | A-119819889 | Included |
| CVE-2019-1994 | A-117770924 | Included |
| CVE-2019-1995 | A-32589229 [2] | Included |
| CVE-2019-1996 | A-111451066 | Included |
| CVE-2019-1997 | A-117508900 | Included |
| CVE-2019-1998 | A-116055338 [2] | N/A to Android 8.1 |
Kernel components
| CVE | References | RealWear Update |
| CVE-2018-10879 | A-116406063 Upstream kernel | N/A to RealWear kernel version |
| CVE-2019-1999 | A-120025196* | N/A to RealWear Android baseline |
| CVE-2019-2000 | A-120025789* | N/A to RealWear Android baseline |
| CVE-2019-2001 | A-117422211* | N/A to RealWear Android baseline |
Qualcomm components
| CVE | References | RealWear Update |
| CVE-2018-11262 | A-76424945 QC-CR#2221192 | N/A to RealWear Android baseline |
| CVE-2018-11280 | A-109741776 QC-CR#2185061 | N/A to RealWear kernel version |
| CVE-2018-11275 | A-74409078 QC-CR#2221256 [2] | N/A to RealWear Android baseline |
| CVE-2018-13900 | A-119052051 QC-CR#2287499 | Included |
| CVE-2018-13905 | A-119052050 QC-CR#2225202 | N/A to RealWear kernel version |
Qualcomm closed-source components
| CVE | References | RealWear Update |
| CVE-2018-11289 | A-109678453* | Included |
| CVE-2018-11820 | A-111089815* | N/A to RealWear kernel version |
| CVE-2018-11938 | A-112279482* | Included |
| CVE-2018-11945 | A-112278875* | Included |
| CVE-2018-11268 | A-109678259* | Included |
| CVE-2018-11845 | A-111088838* | N/A to RealWear Android baseline |
| CVE-2018-11864 | A-111092944* | Included |
| CVE-2018-11921 | A-112278972* | Included |
| CVE-2018-11931 | A-112279521* | N/A to RealWear Android baseline |
| CVE-2018-11932 | A-112279426* | N/A to RealWear Android baseline |
| CVE-2018-11935 | A-112279483* | N/A to RealWear Android baseline |
| CVE-2018-11948 | A-112279144* | Included |
| CVE-2018-5839 | A-112279544* | N/A to RealWear Android baseline |
| CVE-2018-13904 | A-119050566* | N/A to RealWear Android baseline |
Android Security Bulletin — March 2019
Framework
| CVE | References | RealWear Update |
| CVE-2018-20346 | A-121156452 | Included |
| CVE-2019-1985 | A-118694079* | N/A to Android 8.1 |
| CVE-2019-2003 | A-116321860 | Included |
| CVE-2019-2004 | A-115739809 | Included |
| CVE-2019-2005 | A-68777217 | Included |
Media framework
| CVE | References | RealWear Update |
| CVE-2019-1989 | A-118399205 | Included |
| CVE-2019-1990 | A-118453553 | Included |
| CVE-2019-2006 | A-116665972 | N/A to Android 8.1 |
| CVE-2019-2007 | A-120789744 [2] | Included |
| CVE-2019-2008 | A-122309228 | Included |
System
| CVE | References | RealWear Update |
| CVE-2019-2009 | A-120665616 | Included |
| CVE-2019-2010 | A-118152591 | N/A to Qualcomm chipset |
| CVE-2019-2011 | A-120084106 [2] | Included |
| CVE-2019-2012 | A-120497437 | Included |
| CVE-2019-2013 | A-120497583 | Included |
| CVE-2019-2014 | A-120499324 | Included |
| CVE-2019-2015 | A-120503926 | Included |
| CVE-2019-2016 | A-120664978 | Included |
| CVE-2019-2017 | A-121035711 | Included |
| CVE-2019-2018 | A-110172241 [2] | Included |
| CVE-2018-9561 | A-111660010 [2] | Included |
| CVE-2018-9563 | A-114237888 [2] | Included |
| CVE-2018-9564 | A-114238578 [2] | Included |
| CVE-2019-2019 | A-115635871 | Included |
| CVE-2019-2020 | A-116788646 | Included |
| CVE-2019-2021 | A-120428041 | Included |
| CVE-2019-2022 | A-120506143 | Included |
System
| CVE | References | RealWear Update |
| CVE-2019-2023 | A-121035042 [2] [3] [4] [5] [6] [7] | Included |
Kernel components
| CVE | References | RealWear Update |
| CVE-2018-10883 | A-117311198 Upstream kernel [2] | Included |
| CVE-2019-2024 | A-111761954 Upstream kernel | Included |
| CVE-2019-2025 | A-116855682 Upstream kernel | Included |
Qualcomm components
| CVE | References | RealWear Update |
| CVE-2017-8252 | A-112277630 QC-CR#2106159 | Included |
| CVE-2017-8252 | A-114041175 QC-CR#2128529 | Included |
| CVE-2018-11817 | A-114041192 QC-CR#2241830 | N/A to RealWear kernel version |
| CVE-2018-11817 | A-114041747 QC-CR#2166542 | N/A to RealWear kernel version |
| CVE-2018-13899 | A-119053086 QC-CR#2295915 [2] | N/A to RealWear kernel version |
| CVE-2018-13917 | A-120487091 QC-CR#2251019 | Included |
Qualcomm closed-source components
| CVE | References | RealWear Update |
| CVE-2017-8252 | A-79419898* | Included |
| CVE-2017-8252 | A-79420414* | Included |
| CVE-2017-8252 | A-112279542* | Included |
| CVE-2018-11958 | A-114042786* | Included |
| CVE-2018-11966 | A-114042484* | Included |
| CVE-2018-11970 | A-114042111* | N/A to RealWear Android baseline |
| CVE-2018-11971 | A-114042829* | N/A to RealWear Android baseline |
| CVE-2018-13918 | A-120486115* | N/A to RealWear Android baseline |
In brackets is a system reference number that the RealWear technical team uses to refer to each issue.
• [HMT-2239] Translation suggestions for Polish language after first testing of V10 Early Access
• [HMT-2347] [JP Translation] My Controls Set Level for Volume/Brightness commands differ from what is shown
• [HMT-2349] [JP Translation] Numbers screen on keyboard are an erroneous mix of Japanese and English
• [HMT-2446] [Spanish (US) Language Translation] Various problems with Spanish translations
• [HMT-2456] [Language-Chinese] Incorrect translations for “Video Forward” and “Audio Forward”
• [HMT-2458] [Language-Polish] Wrong translations for “Zoom Level”, “Delete”, and “Confirm”
• [HMT-2499] [Language-ZH] ‘Slave’ string in Chinese is mistranslated
• [HMT-2508] [Language-TH] Audio Forward Voice Command Mistranslated
• [HMT- 2511] [Language-DE] German Voice Commands for SECURE ENTRY and NORMAL ENTRY could be improved
• [HMT-2523] [JP Translation] Various issues with translation
• [HMT-2594] [Language-Russian] Native Speaker Translation Corrections
• [HMT-2596] [Language-Italian] Native Speaker Translation Corrections
The list below indicates the issues fixed in this release. In brackets is a system reference number that the RealWear technical team uses to refer to each issue.
• [HMT-1508] Mute Microphone – Microphones are not muted after resuming from sleep.
• [HMT-1841] Badge selection doesn’t work for toggle button under settings.
• [HMT-1997] Home screen year is truncated to last 2 digits. Updated to display 4 digits.
• [HMT-2199] MyCamera Photo Preview Animation leading to delayed or missed speech commands.
• [HMT-2205] Document Viewer crashes upon opening content URI provided by File Provider – FIXED. One symptom of this bug was that an error would appear when opening some .pdf files, “Password protected PDFs not supported” even though the file was not password protected.
• [HMT- 2211] Toast (pop-up notifications) interferes with Custom Voice Commands in firmware upgrade 10.0.0-08-C.HMT-1.G.
• [HMT-2302] Passing URI to My Camera via intent causes application crash.
• [HMT-2303] Menu Items in standard Android overflow menus do not get recognized automatically.
• [HMT-2304] Unable to open no password protected PDF file in HMT, says “Password protected PDFs not supported”.
• [HMT-2305] [Language Korean] Voice command for Zoom level in Camera or configuration app is not working.
• [HMT-2306] [Language Korean] Voice command for select item is not working.
• [HMT-2307] [Language Korean] Voice command for Set level in Brightness or Volume does not work in Korean Language.
• [HMT-2351] In Japanese keyboard, ‘Scan Code’ screen causes WearHF crash/ unresponsive voice commands.
• [HMT-2359] Custom Commands and BNF tree refresh issue. Custom commands that worked before the microphone auto-muted must continue to work after the auto-mute is restored.
• [HMT-2395] [Language-Spanish] Set Level Voice command is not recognized.
• [HMT-2449] Incorrect error message when using file provider when capturing video. Camera app shows a message saying file providers aren’t supported … or … If is implemented, camera app records to the file in the file provider.
• [HMT-2478] With Wearhf 2.0.20-23 : show help does not work on many 3rd party apps.
• [HMT-2481] Too many accessibility events triggered in logs when we launch and scroll through PIN Unlock screen.
• [HMT-2482] Homescreen Background – When deleting the homescreen_background.json file, the file used for the background is incorrect and overlaps the time.
• [HMT-2509] ABC Mode – When switching to ABC mode the command pop-up is wrong.
• [HMT-2513] ABC Mode – Symbols section does not preface the symbols with “SYMBOL…”.
• [HMT-2515] Videos captured by Intent show wrong filename when saved.
• [HMT-2516] Listcontrol moves too much left and right.
• [HMT-2520] [Wi-Fi] In Password entry screen, ABC mode is set by default and VC to enter characters doesn’t work.
• [HMT-2529] Keyboard – Japanese Language – Letters – Only 3 Japanese letters are displayed.
• [HMT-2537] Images captured by Camera applet options are not accessible in My files, unable to open and view the images.
• [HMT-2538] Crash is observed in logs when we take photo from Camera applet option in Developer Test apk.
• [HMT-2564] Badge Number and select item 1..# option is not displayed in My Files.
• [HMT- 2566] “My Documents” “My Media” & “My Photos” are not translated as per the HMT language set and voice commands fail to open.
• [SUP-20] When Recording Video to storage capacity, device becomes unusable.